two-step verification
Two-Step Verification
The two-step verification feature adds an additional level of security to Google Apps' user accounts by asking them to enter a verification code
in addition to the user name and password when signing in/logging into their account.
Two-step verification helps protect a user's account from
unauthorized access if a person succeeds in obtaining the password. Even
with password penetration, speculation, or attack in any other way, an
attacker could not log on without entering the user's verification
codes, which only the user could obtain via mobile phone.
This can be done through the following steps:
- Login to account information on the Mail page.
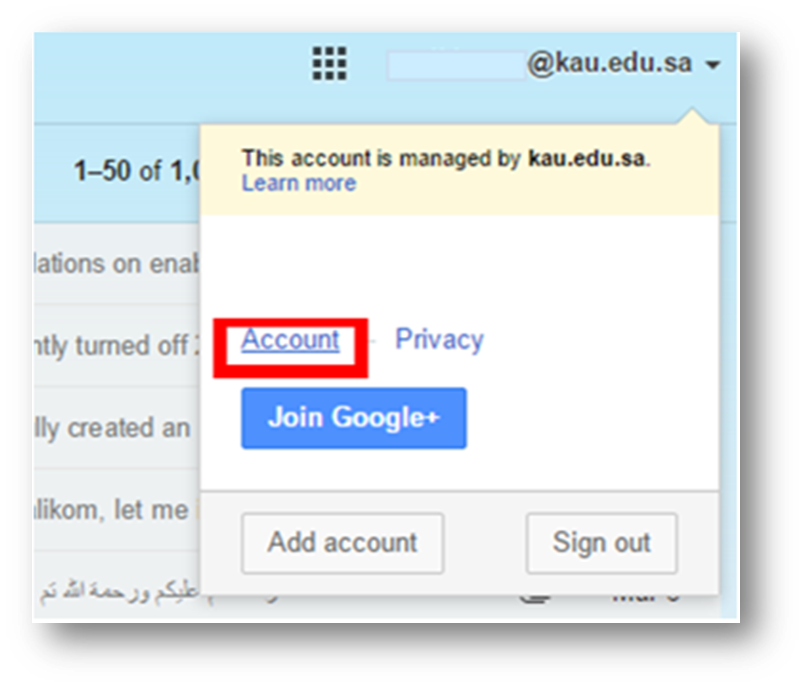
- Select the two-step verification.
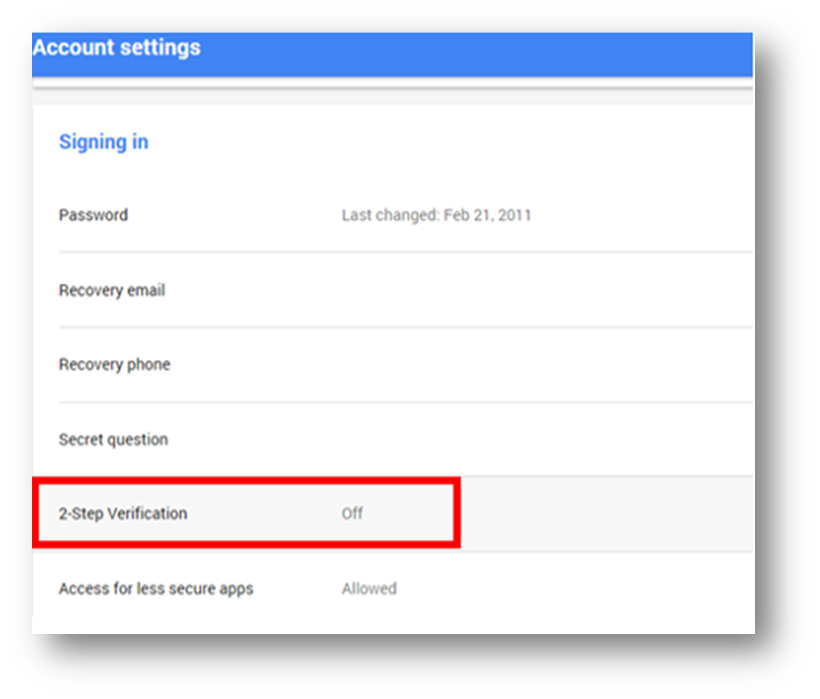
- Click Choose to start the steps.
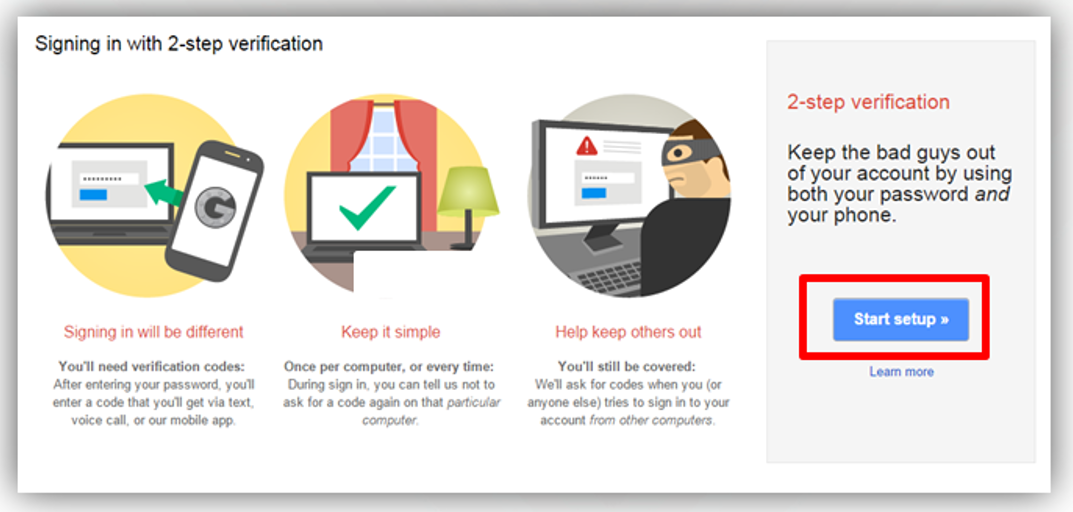
- The user registers his or her phone number and determines how the verification code is received through his mobile
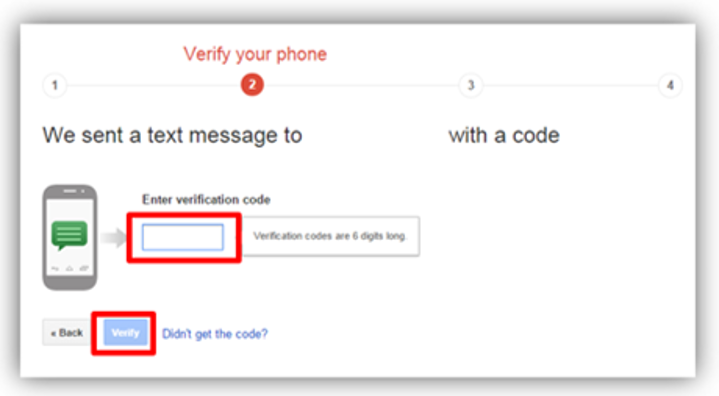
phone, a text message or a phone call, and then press (send code).

- After that you will receive a message with 6 digits which is placed in the assigned box in order to complete the verification process (Verify).
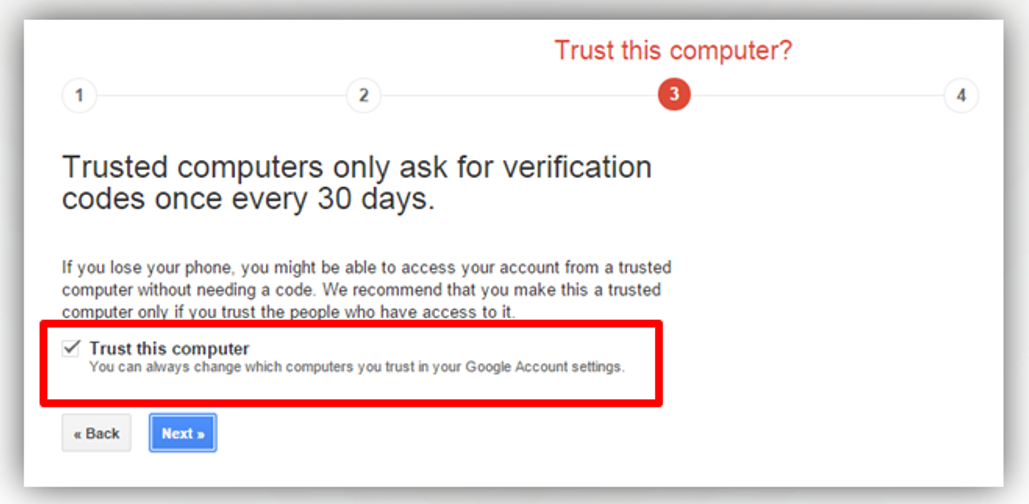
- When the user chooses that this device is a trusted Computer "trust this computer", he will only be required to enter the verification code once every 30 days or after the browser's cookies have been deleted.
The user must not specify this option if he or she is working on a public or shared computer.
- The next time a user logs on to his or her Google Apps account with a new browser or device, he or she can enter his username and password as usual. It is then claimed in another
window to enter the verification code. Here the device can also remember the one-time verification code once every 30 days.

- When you log in back to the two-step verification settings, other options will appear.
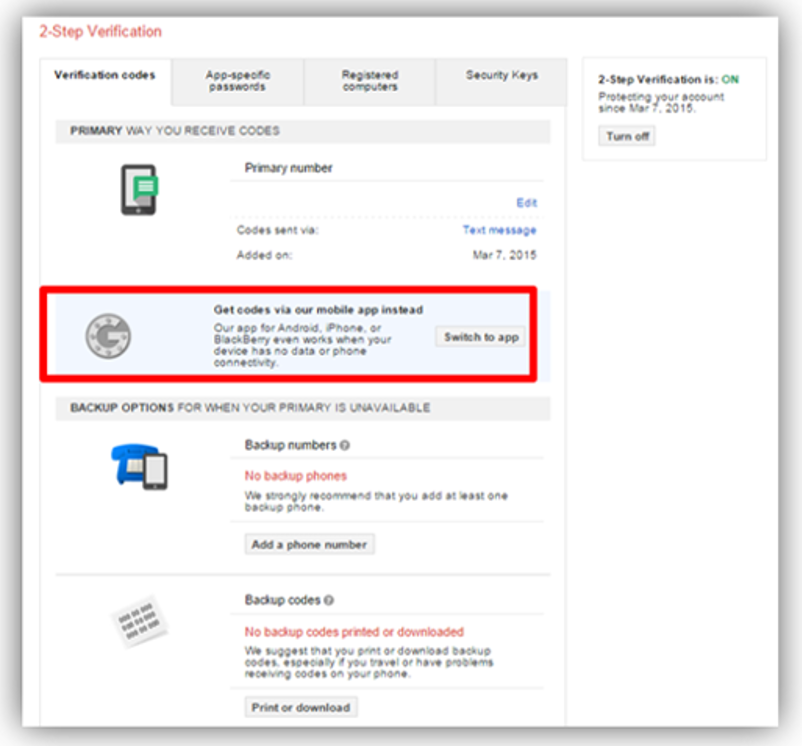
- Users of smart phones can use the Google Authenticator application, which can create offline icons for the network.
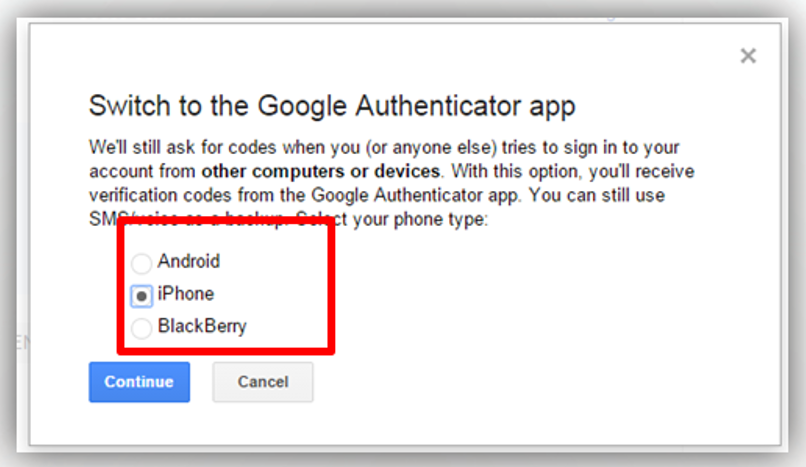
- When choosing this application (Google Authenticator) you must specify the mobile type and then continue.
- Then download the Google Authenticator application on the mobile. You can find its link in the window and follow the instructions.
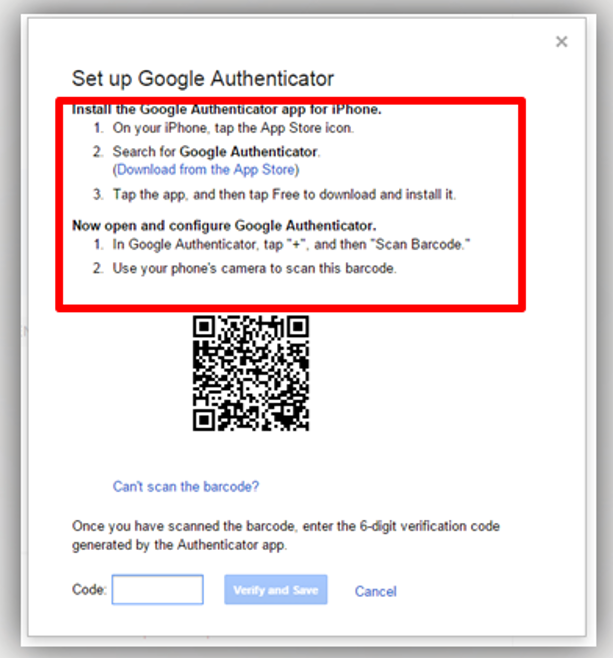
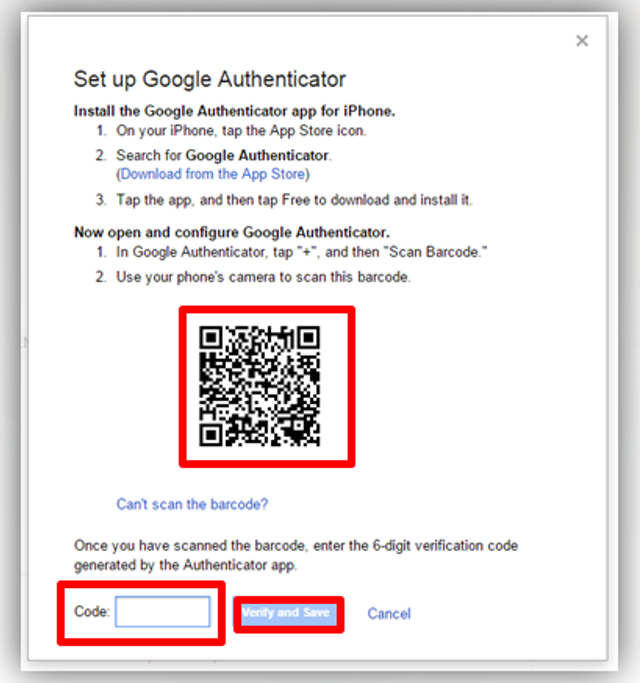
- The Google Authenticator application opens on your mobile,
then scan the bar code in the window. After that, you will
receive a 6 digits code on the mobile, which should be placed in
the custom box to be verified and saved.
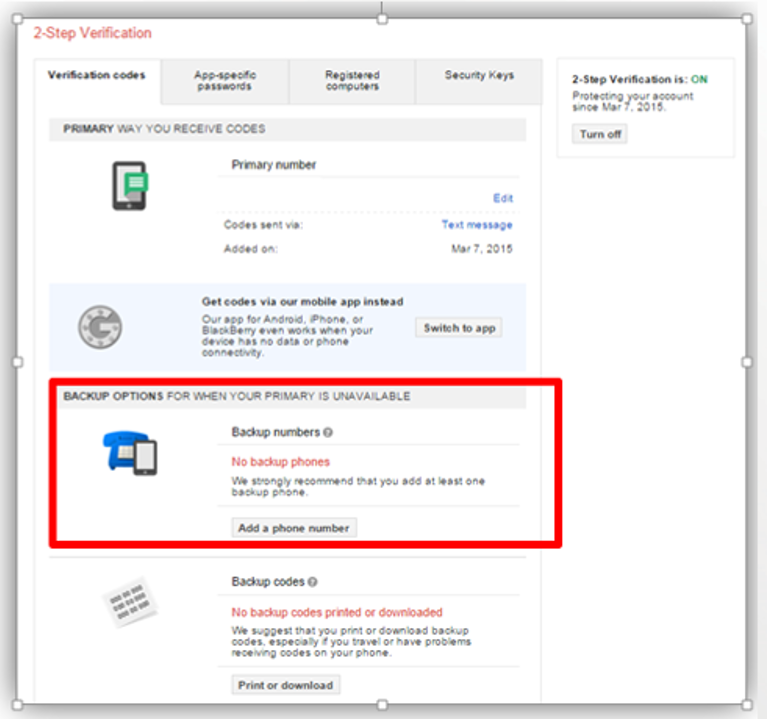
- You can also add another phone number to receive the verification code, which is necessary in case your phone is lost.
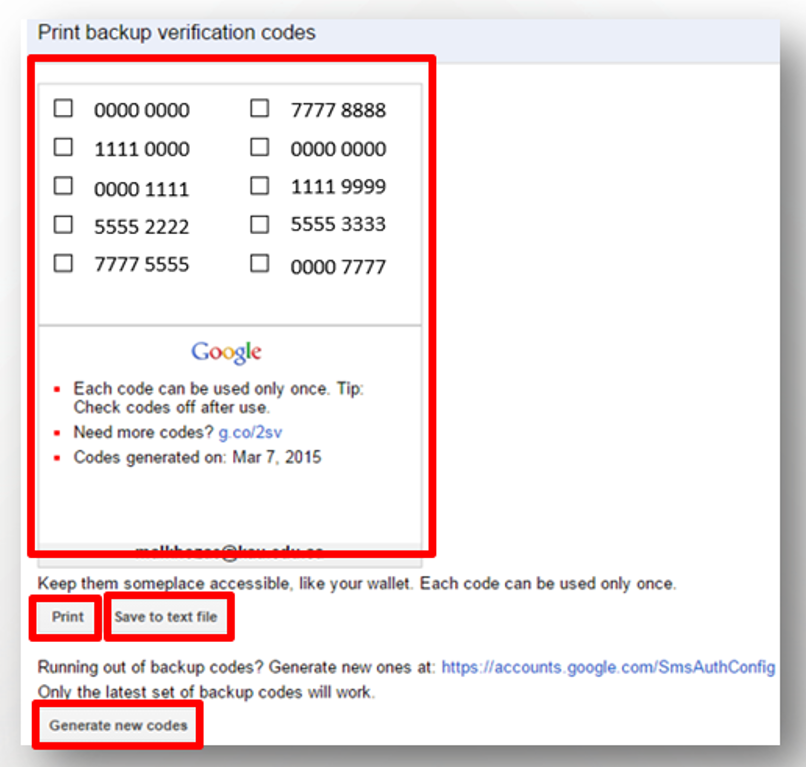
- When the user loses his phone, he can log on using backup codes.
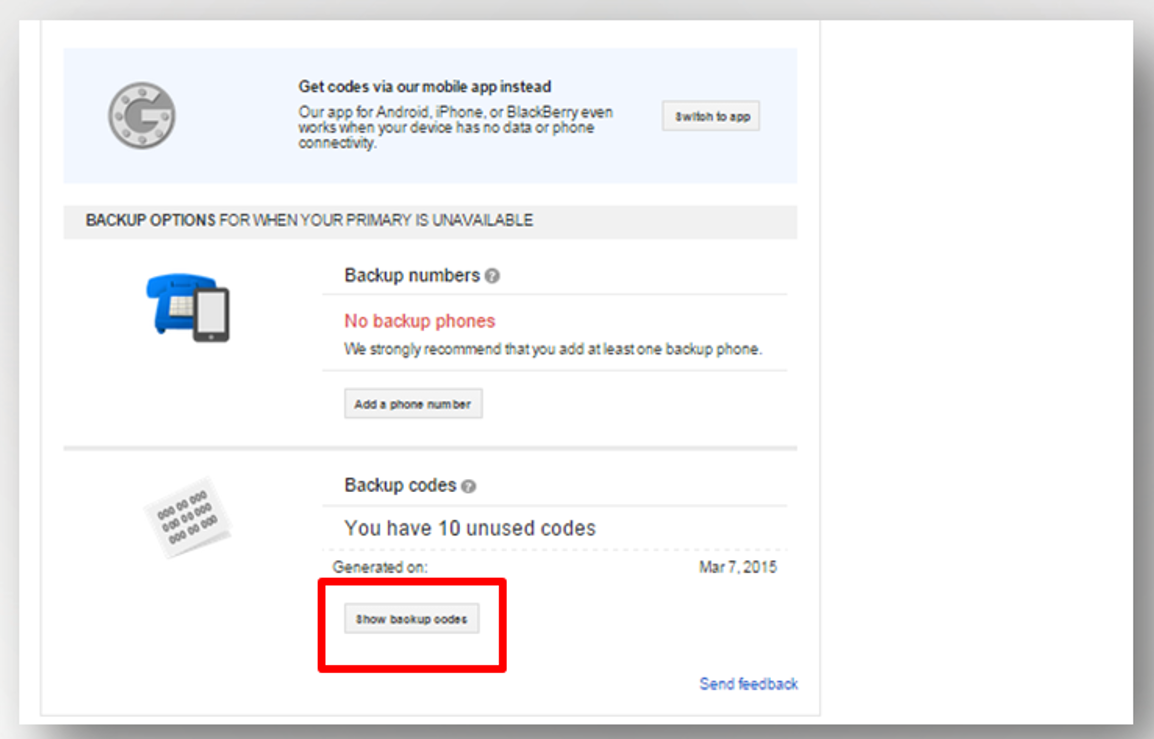
- Backup codes will appear to the user and thus they can be saved, printed, and retained. Each code is only used once, and new backup codes can be created through (Generate new codes).
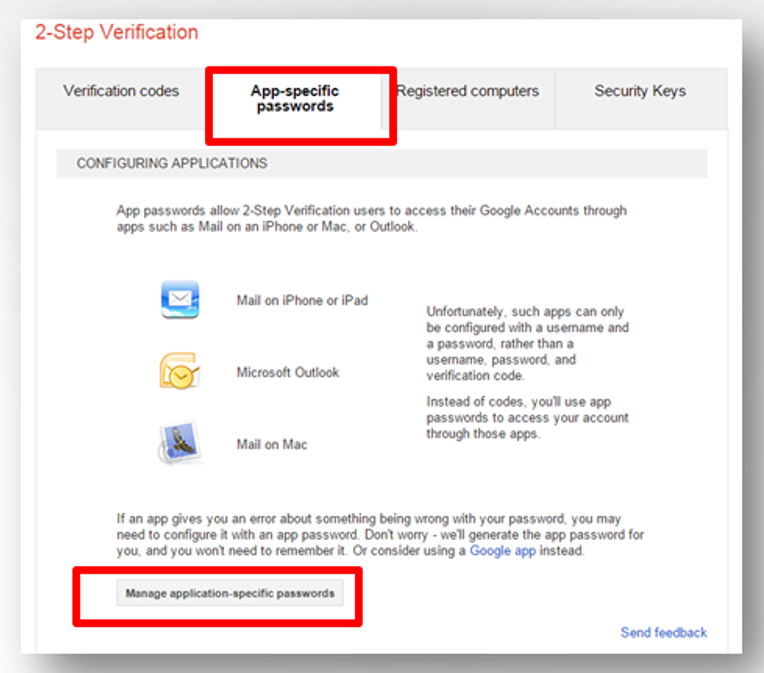
Sign in to mobile phones using –The specific passwords for the applications/the application-specific passwords:
Once users sign up for the two-step verification, they may need to use the application-specific passwords in addition to the one- time verification codes per Device or application; this can be used as an alternative of the usual password, so that they can access their accounts in Google.
You can log on to Google apps on mobile phones using your application-specific passwords, through:.
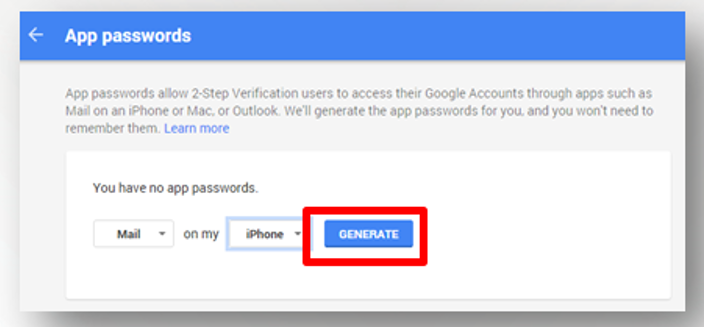
Choose Application-specific passwords then Manage application-specific passwords.
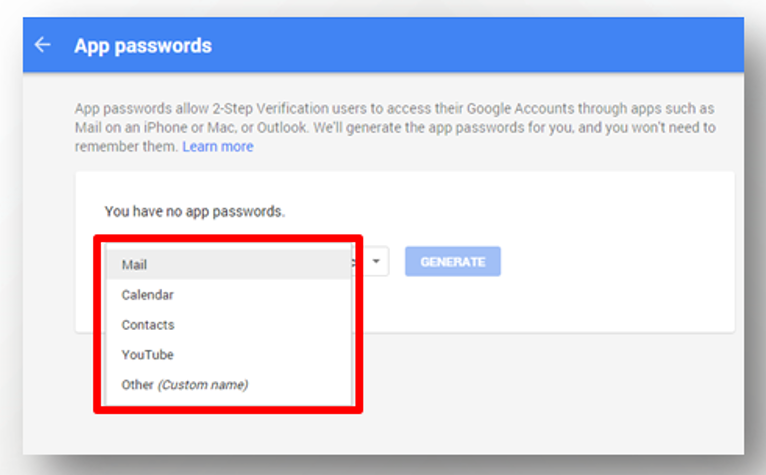
Choose an application (Example: mail application).
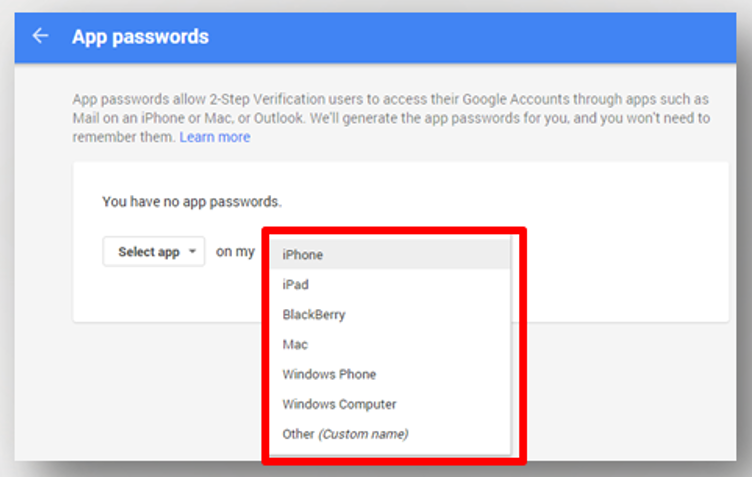
Choose the device type (Example: iPhone).
Create password.
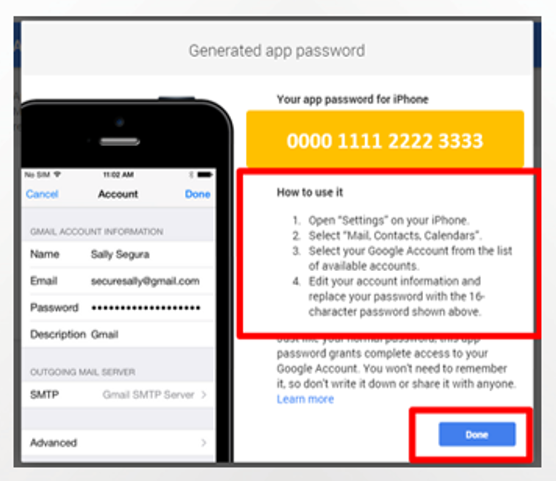
A window that has the mail application's password will appear and how it should be placed/entered in the phone instead of the
password of the user name, without spaces, and then click finish.
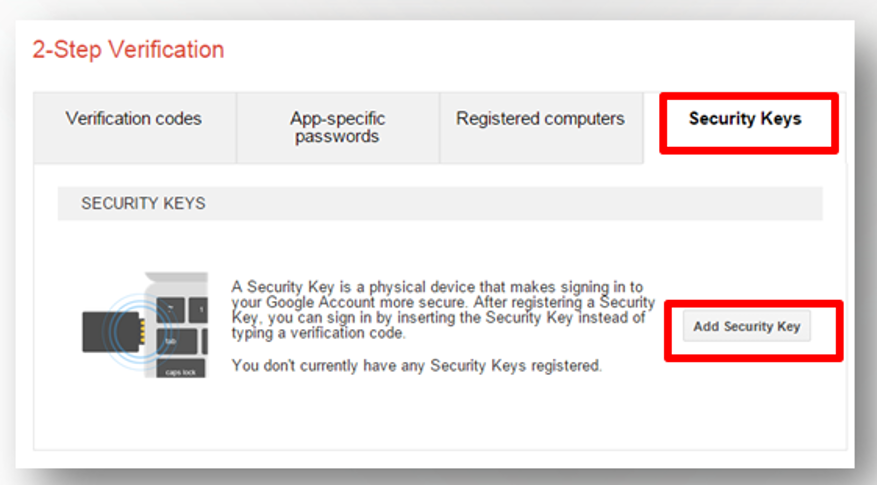
Security key:
The security key can be chosen as a private primary key instead of
the verification codes sent to the phone. This can be done through:
- Choose security key then add security key .
- Follow the instructions in the window below, and then insert the security key for the computer USB port and register.
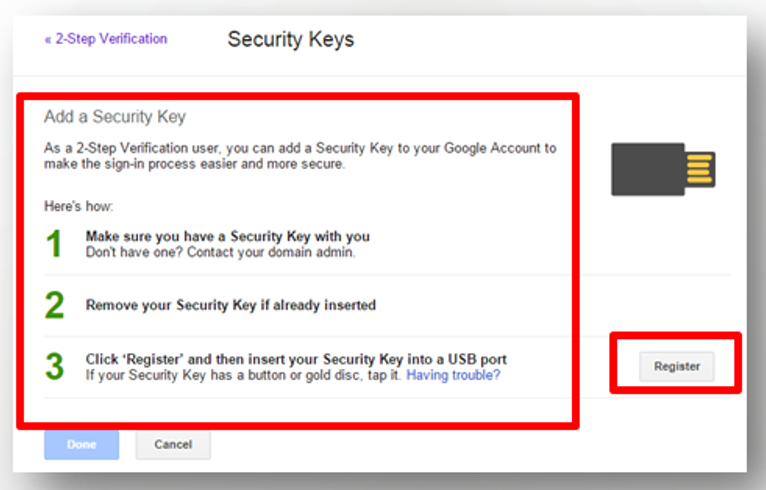
- After completion this key will be the verification code and must be placed on the USB port in your computer to verify the user.
Register devices as trusted (Registered computers):
When you activate two-step verification, a message will appear to choose the current device as reliable, as was mentioned earlier. Consequently,
the device will appear as trusted in the following window, and the verification code will not be requested when you access again- for 30 days.
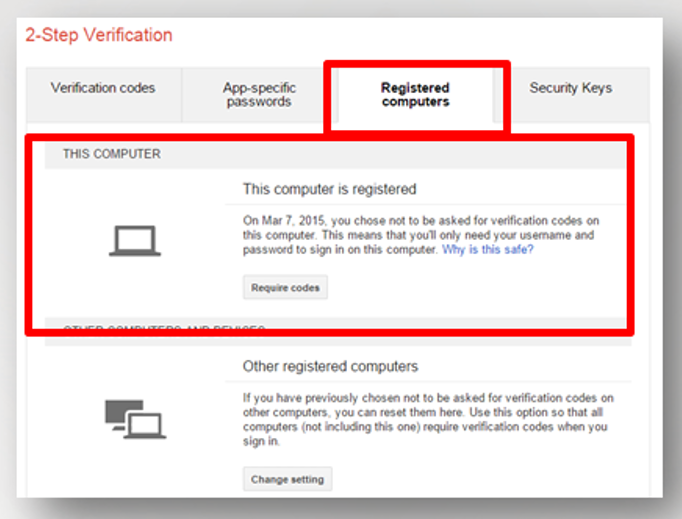
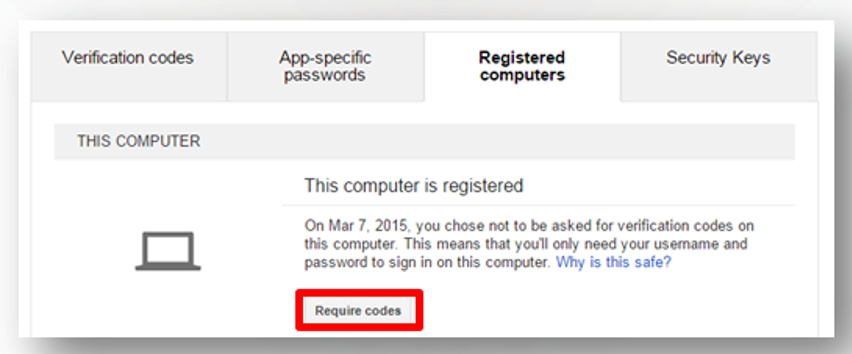
The reliability of this device can be removed by choosing require codes and remove this computer from my trusted list.
Other devices that have been placed as a trusted device can also be identified and removed.
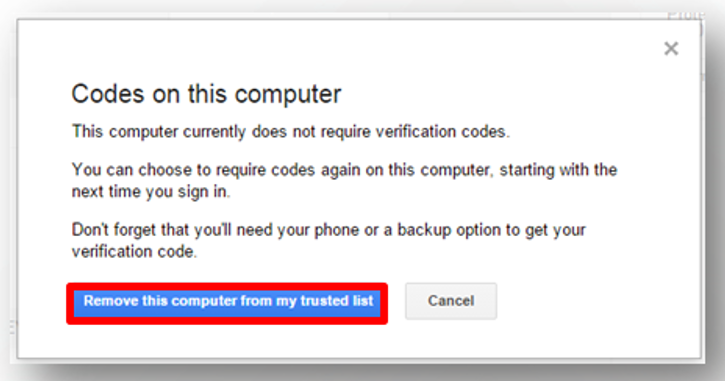
Other devices that have been placed as a trusted device can also be identified and removed.

|
Last Update
4/25/2018 1:32:55 PM
|
|
|
|